Azure Sphere
“An edge device or sensors needs to be secure and just work!”
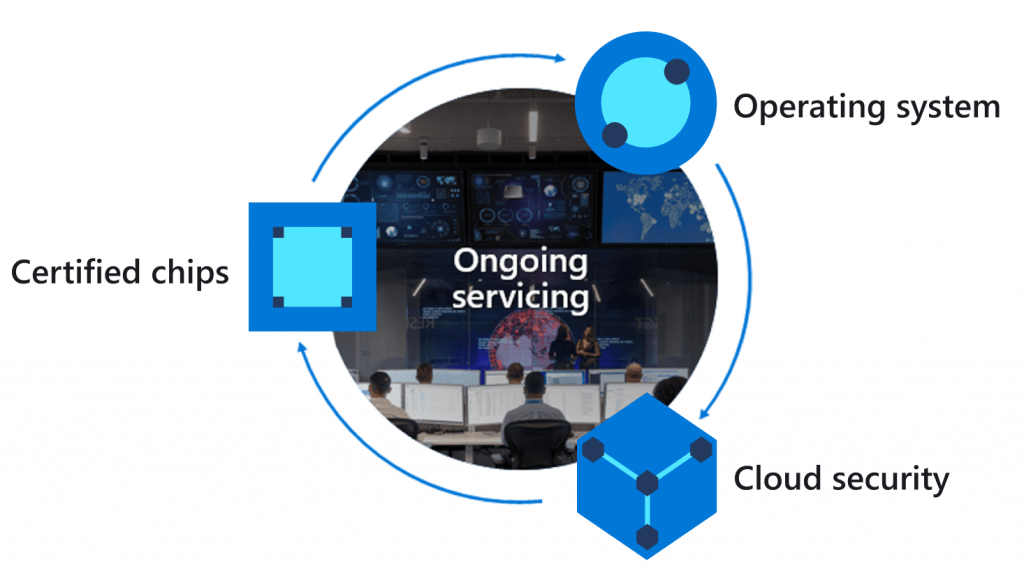
IoT is about connection and unfortunately, most IoT devices are very vulnerable. Microsoft has a unique solution called Azure Sphere which has 3 components: specialized hardware, special operating system, and cloud components—to actively protect your IoT devices, your business, and your customers. Have a look at https://azure.microsoft.com/en-us/services/azure-sphere/ to get a picture of what it is and how it works.
If you would like to hear more about all the opportunities for you and your projects, feel free to contact us as we are developing huge knowledge in this area and we already have specialists for Azure Sphere. This could be a game-changer for your devices and business as nobody wants to be hacked and lose sensitive data.
The seven properties of highly secured devices
Our research on bringing high-value security to low-cost devices identified seven essential properties needed to make devices highly secured. Easily build these properties into your IoT with Azure Sphere.
-
Hardware-based root of trust
This guarantees that a device is running only genuine, up-to-date software before it can connect to the rest of the internet.
-
Defense in depth
More layers of defense make it harder for an attacker to gain access to a device’s most sensitive secrets. More sensitive areas are put behind greater layers of defense.
-
Small trusted computing base
A trusted computing base should be kept as small as possible to minimize the surface that’s exposed to attackers and to reduce the probability that a bug or feature can be used to compromise it.
-
Dynamic compartmentalization
Boundaries between software components can prevent a breach in one component from propagating to others. Dynamic boundaries can be moved and redrawn safely.
-
Certificate-based authentication
Passwords can be the weakest link in many security systems. Certificate-based authentication eliminates the need for passwords to manage a device.
-
Error reporting
Early detection, analysis, and response to errors is critical to stopping threats before they cause significant damage.
-
Renewable security
The ability to deploy ongoing software updates is essential to tightening a device’s defenses and shutting down vulnerabilities.
